LTC VIDEO SURINDER - BRIGHT (1)_1 (1).mp4
Support 24/7
Delicated 24/7 Support
Easy Returns
Shop With Confidence
Card Payment
12 Months Installments
Standard Shipping
Capped at 100rs per order
Support 24/7
Delicated 24/7 Support
Easy Returns
Shop With Confidence
Card Payment
12 Months Installments
Standard Shipping
Capped at 100rs per order
Featured Categories
Featured Products!
Community Top Picks


Popular Categories
sfdfsf.jpg)
Customer Review
As a customer, I am happy with the keyboard I bought from Prodot's website. I've been using it for more than 4 years now, and there haven't been any issues to speak of. I must say they have quality products.

Rahul Yadav
Customer
Prodot's products have improved my work efficiency. The ergonomic design of their keyboards is fantastic, and the durability of their mouse is impressive. Worth the investment!
.png)
Shivam Jha
Customer
Great built quality and very well coated. Me and my friends work and play games over the servers and we have been looking for a good quality cable and so far it has not shown any problem. Highly recommend.

Sourabh Gupta
Customer
I have been using the made in India keyboard for a while now and I must say I am impressed with its quality and performance. The print quality is top-notch and the fact that it is made in India. I highly recommend to buy.
.png)
Anjali Sai
Customer
In The Talks

Common Cctv Cable Issues And How To Fix Them
Whether for personal or professional use, ...
.jpg)
The Future Of Laser Toner Printing Technology: Innovations On The Horizon
Laser printing was developed in the late 60s by Xerox Corporation, but the first commercial laser printer was released in 197...
.jpg)
The Importance Of Ergonomic Keyboards In Reducing Typing Strain
Does your work entail spending long hours working on a keyboard ? Do you feel pain in your wrist after hours of typing? Did y...
.jpg)
How To Set Up And Optimize Your Wireless Keyboard And Mouse
In today's whistle-stop and digital world, where every single thing is at your fingertips, a ...
2.png)
How To Extend The Lifespan Of Your Laser Printer Toner
Let’s be honest laser printer toner can be costly. Printing costs ca...

Reviews Of The Best Selling Made In India Computer Accessories
The proliferation of technology has meant only one thing: a demand for top-of-the-line computer p...

Frequently Asked Questions About Toner Cartridges Answered
Toner cartridges are the invisible engine behind every clear, smudge-free print. Whether its preparing a business slideshow or pri...

Tips For Extending The Life Of Your Printer Cartridges
Printer cartridges are an essential tool for seamless printing whether in your home or office. The thing is, however, the const...

Future Of Wireless Mice Trends And Predictions For 2025
Wireless mice have seen so much change in the last few years. Today, for professionals and gamers, it's a crucial tool, just l...

Difference Between Generic And Original Printer Cartridges
As the demand for printing goes up, the need for printer cartridges also increases, leading many users to think about cheaper...

The Role Of Oems In Product Quality And Safety For Computer And Laptop Accessories
In the fiercely contested markets of computer and laptop accessories, the quality and safety of t...

How A Made In India Company Ensures Quality In Computer Accessories
With the increasing number of local players willing to manufacture high-quality products at a cos...

Enhance Your Cctv Surveillance With High Quality Cctv Camera Cable
These days, a lot of us equip our offices and homes with cctv cameras. Few people are conscious, though,...

Maximize Productivity With Hp Original Toner Cartridges
Being a top supplier of ink and toner, Prodot knows how ...

5 Amazing Benefits Of Choosing Original Equipment Manufacturer Products
Whether your machinery is new or used, making sure it receives the right upkeep is crucial to its durability and effec...

Wireless Vs Wired Mouse Whats The Best Option For Your Needs
A wired mouse was undeniably superior back then. It was a plug-and-play system that functioned as expected and would...

Unveiling The Leading Oem Manufacturer
Indias Pinnacle of Manufacturing Excellence – Unveiling the Leading OEM Manufacturer...

Exquisite Professional Range By Prodot A Made In India Company
Indias computer hardware business is experiencing rapid growth, with both domestic and foreign businesses participating in the ...

Buy The Best Made In India Computer Accessories Online
In both personal and business settings, laptops have surpassed desktop computers in popularity because of their portability and...

Prodot Group: Uncovering Innovation At The Expo
For global businesses looking to showcase their state-of-the-art products and services to an international customer base, the I...

The Spl 2 - A Magnificent League.
Sports are indisputable when it comes to a persons overall development, regardless of how much we may argue that academics are ...

1 Year To India’s G20 Presidency Today: Reflections If Any
As India marks the one-year anniversary of its G20 presidency, its an opportune moment to reflect on the achieve...

Dos And Donts Of Organising Your Cctv Cables For Winter
As winter approaches, its essential to pay attention to the maintenance of your CCTV camera system, particularly organising of ...

How Many Times Can You Refill A Printer Cartridge
In the ever-evolving landscape of modern technology, printers remain indispensable machines for both personal an...

Can Wireless Mouse And Keyboard Work Together
In todays tech-driven world, the demand for seamless and clutter-free computing peripherals is higher than ever....

How Do I Choose A Usb Hub
In todays digital age, a USB hub has become an essential...

Prodot Group At Ifsec India Expo 2023
As a major global provider of security and fire event solutions, IFSEC India has been th...

How To Calculate The Page Yield Of A Cartridge
When choosing the right printer cartridge, understanding page yield is crucial. Page yield denotes the n...

How To Connect A Wi-fi Dongle To Pc
Connecting a Wi-Fi dongle to your PC is a straightforward process that can greatly enhance your com...

Stay Safe Three Things To Know About Extension Cords
In our tech-driven world, extension cords are indispensable for powering devices. As online shopping grows, buying them digital...

Get Rid Of Tangled Wires With The Prodot Wireless Keyboard And Mouse Combo
In the era of advanced technology, the convenience and efficiency of wireless devices have revolutionised the way we...

Hp 88a Black Laserjet Toner Cartridge: Prinitng Made Easy
In the fast-paced world of business and personal printing, the choice of a high-quality toner cartridge can make a ...

Click With Precision Discover The Best Wireless Mouse In India
In todays fast-paced digital world, a wireless mouse has become an indispensable tool for enhancing productivity and p...

How To Refill Ink Cartridge
Printer cartridge essential components of any printing device, containing the ink necessary for producing high-quality prints....

Laser Toner Cartridges
A toner cartridge, also called laser toner, is a consumable component for laser printer. It is entirely different from ordina...

Buy The Best Extension Cord With Usb And A Combo Of Wireless Keyboard And Mouse Online
ProDot has more than 10+ models of best extension cord with usb that are used to protect equ...

Women At Prodot Saluting Womanhood
At Prodot, we celebrate our women everyday! Here we are a team of Pro-Women. There’s a thing about strong wome...

Prodot Laptop Adapter
AC Laptop Adapters are electronic devices used as charger. It is an external power supply connected w...

From Wireless Mouse To Printer Cartridge The Best Available Option In India
To help you seamlessly navigate across your screen, a mouse is an important input device for your PC. ProDot has...

How Can You Assure Security At Your Homes And Offices
When it comes to installing a security or surveillance device, selecting the best CCTV camera cable in Delhi is ...

Prodot An Initiative Towards Atmanirbhar Bharat
Are you looking for a Best Wireless Mouse For Laptop? Are you looking to grow your Information Technology Busine...

Prodot Participates At Imaging Products Exhibition At Bangalore
Delhi [India], December 4: The ‘Biggest Exhibition of Imaging Products’ is ...

Prodot Your Trusted Computer Manufacturer In India
In these dynamic times which are accompanied by new challenges and increased workload, people are getting tougher. In order to ...

Are You Looking For A Keyboard And Mouse Combo
In these dynamic times which are accompanied by new challenges and increased workload, people are getting toug...

A Beginners Guide To Buying The Right Adaptor For Your Laptop
With innovations and inventions, the range of options for the best laptop charger online in India ...

Get The Wireless Keyboard And Mouse Combo For Your Computer
Your desktop is incomplete without a well-functioning keyboard and mouse. The quality of your mouse and ke...

Get Six Socket In Prodot Spike Buster
Do you see gadgets, computers & tech devices all around you? These devices have become a part of our lives...

Are You Looking For A Replacement Of Your Defective Mouse
Currently, businesses run because of the technologies developed. If any of the tech products stop working, our...

Do You Know The Difference Between Printer Ink And Toner
Knowing which brand of printer ink and printer toner you are using for your printer is important. ...

Mouse That Will Make Your Work Swift And Easy
Is Your wired mouse causing difficulty in your work? Are you unable to extend your hand after a certain...

Do You Check The Safety Of Your Electronics Products Before Buying
While buying any electronic or tech product, people are conscious of the safety of the product and of thei...

Replace Your Tech Products In Just 5 Minutes
Imagine your tech product stops working after one month of buying. What will you do next?...

Facing Difficulty With Your Printer Check Here What You Need To Do
Post-Covid Lockdown, clogging of inks has been one of the most popular problems in the corporations that disrup...

Are You Looking For A Perfect Wireless Keyboard And Mouse Combo
Check here When your Keyboards are swift, your work finishes swiftly and smoothly too. Computers h...

Optical Mouse Quad Relaxation In Symmetry
In layman language the term QUAD or quadrangle is used to define something which has four corners and a closed figure. S...

Palm Wireless Mouse Comfort Grip For Your Palm
Prodot brings an update in these new year festivities. It’s launched a wireless optical mouse named the Palm, providin...

Initiative To Better Lives Yaidiwalialagnirali
Initiative To Better Lives #YaidiwalialagniraliA strong sentiment of helping local shops and s...

15 Reasons Why Should You Go For Make In India Products
You would have heard/read the news where PM urges to opt for local products and make India self-reliant. It doesn’t me...

Prodot Group Agrees On Vocal For Local
Earlier on May 12, Prime Minister Modi emphasised on the use of Indian products to make India self-reliant in the coronavirus...
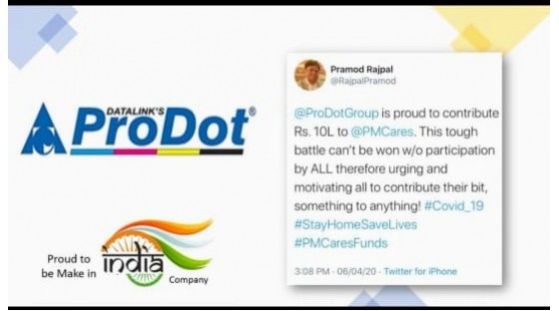
Prodot Contributes One Million To Pm Cares Fund
ProDot, the only Cartridge Manufacturer in India today announced that it has contributed Rs.One Million towards the Prim...

Inking The Country Blue With Prodot
What began as an iconoclast blue-themed brand in mere 50 sq. ft. holding raw ma...

Prodot Launches New Products In Its Partner Meet In Dubai
Prodot, the brand name of Datalink Industrial Corporation is an ISO 9001:2015; CE and FCC certified company based out of...





















































.png)



.png)
.jpg)

.jpg)

.jpg)

.jpg)



